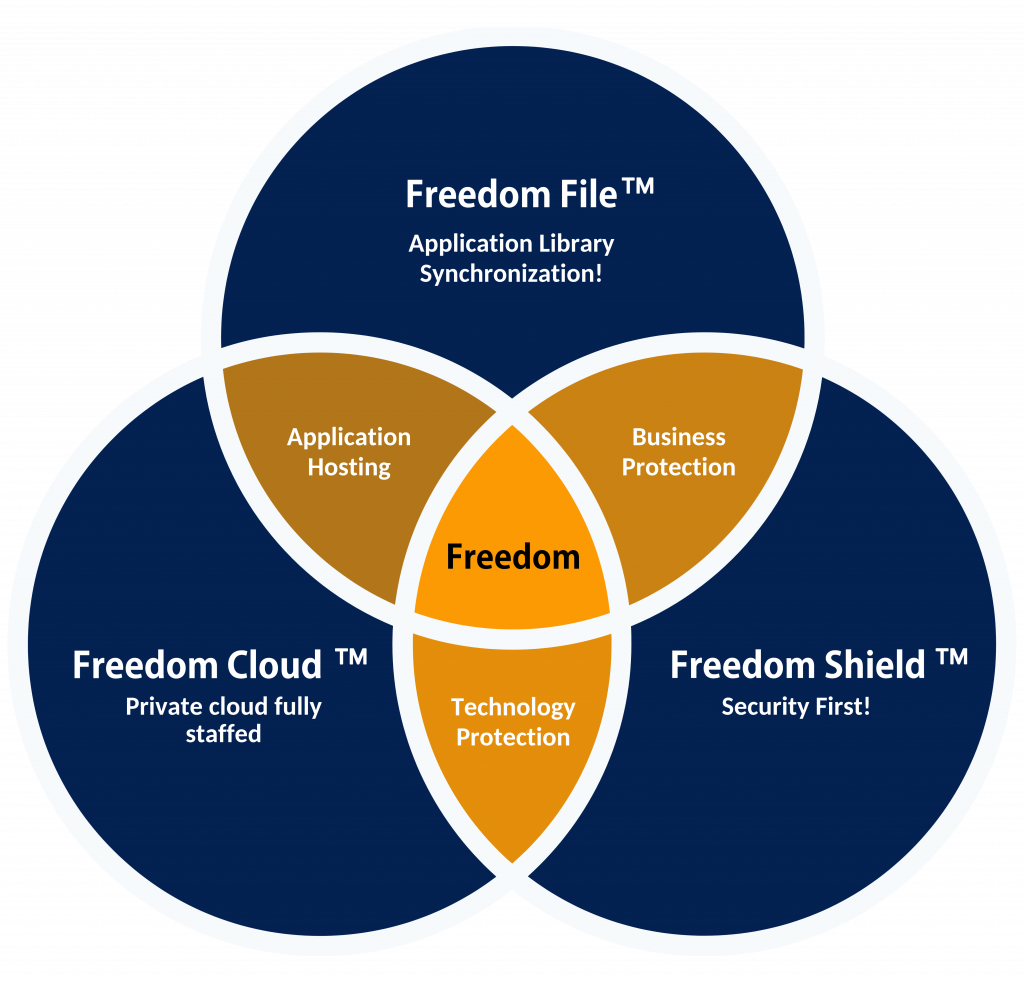
The Freedom System: Fully Managed & Secured Application Desktops
With A Continuous Risk Management Process
Providing Cost-Effective & Secure Solutions to SMBs Throughout the US Since 2004
SMBs often find themselves spread too thin.
Freedom Cloud™ provides virtual desktops to meet the demands of thousands of SMB users. This saves money and increases productivity without compromising security.
As IT Experts since 2004, iStreet Solutions believes that technology should ‘just work’. When it does, time can be better spent to focus on achieving business goals.
Empowering SMBs to Focus on Meeting Business Objectives and Solving Their Customer Needs
Providing Secure Application Access
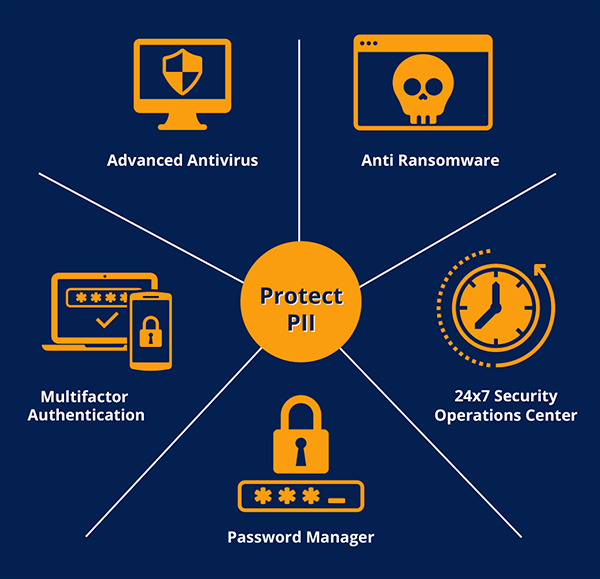
Protecting Personally Identifiable Information (PII)
Freedom Cloud™ Total Cost of Ownership (TCO) reduces cost of IT staff and information technology hardware. Using the secured virtual desktop, the board and staff can escape the troubling cycle of procuring, installing, configuring, operating, upgrading and replacing technology. This gives employees more free time to concentrate on the mission of the organization.
Freedom Cloud offers BGC non-profit organizations enterprise class security, backups, and disaster recovery, allowing them to reduce technology risk and manpower at a much lower cost.
Addressing Cyber Security Risk and Insurance Underwriting requirements
Critical Data is Secured on the Centralised Host
Data Storage/Backup
File Sharing

Secured Access to Email & Productivity Applications

Cloud Computing for Business Applications such as:


Managing Risk Beyond The Insurance Policy
Identify

Vulnerability Scanning and Pen Testing
Identifying and fixing cyber weaknesses. Enabling the business to better its systems and data from malicious attacks.

Phishing and Cybersecurity Training
Human Error is still the driving force behind majority of cybersecurity problems.

Log Collection and Management
Identify and Isolate malicious activity quickly. Detect attacks and security misconfigurations.

Intrusion Detection System
- IT Monitoring function with off-hours alerting
- Basic security monitoring capability (AV alerts)
Analyze

Information Security Policy
Rules and procedures for all individuals accessing and using an organization's IT assets and resources.
Business Continuity Planning
- Proactive business process to understand potential threats, vulnerabilities and weaknesses to react quickly and efficiently to business interruption
- Annual Incident Response Plan Review

Virtual CISO
- Experienced and Trusted Cybersecurity Team
- Review and Revise Current Security Policies and Procedures
- Ensure Compliance with Industry Regulations like SOC2, CMCC, HIPAA and PCI
Control

Privileged Access
- Secure against unauthorized access to critical assets
- Restricted User Rights
- Separation of Admin Accounts

Endpoint Protection
- Real-time Threat Protection
- Spam and Phishing Protection
- Communication Confidentiality
Firewall
Filtering and monitoring of web traffic and email traffic.

Patch Management
- Monthly Patching Schedule
- Defined Cadence of Vulnerability Scanning
- Inventory of Unpatchable Systems

Backup 3-2-1
Ensure recoverability when it is needed most.
- 3 Copies of Data
- On 2 different media
- 1 Copy off-site

Password Control
Storing and managing passwords efficiently to prevent unauthorized access.

Multi Factor Authentication
- More layers of security than 2FA
- Meets regulatory compliances
- Reduce fraud and identity theft
IS YOUR CYBER SECURITY GIVING YOU SLEEPLESS NIGHTS?
Click here for a Free Cybersecurity Vulnerability Assessment
Partner with iStreet Solutions, provider of Freedom Cloud™. Ensure your organization is in control of your PII and critical data.




